Published Nov 03, 2022 by Xiph
Of all cyber attacks that occur, none are more difficult to mitigate than denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks. These attacks can bring down even the largest websites (including Google) by overloading servers with traffic requests and sending networks crashing down.

Denial-of-service attacks can strike any website or online operations at any time which is why it’s important to recognise the risks and know how to prevent these malicious attacks. We cover everything you need to know below.
What’s a denial-of-service (DoS) attack?
A denial-of-service (DoS) attack is a malicious attempt to overwhelm a device, information system, or other network resource and render it inaccessible to its intended users. DoS attacks aim to disrupt the normal operations of devices or networks by flooding the targeted host or network with superfluous traffic to overload systems or trigger a crash ─ resulting in a denial-of-service to intended users. In layman’s terms, this prevents legitimate users (i.e. employees, customers, or account holders) from accessing expected services and resources. DoS attacks can target specific infrastructure, network applications, and other systems such as industrial control systems (ICS).
DoS attacks can last anywhere from a few hours to months and can cost businesses and organisations millions if their resources and services remain unavailable to their intended customers, and users.
What’s the difference between a DoS attack and a DDoS attack?
The difference between a DoS and DDoS attack is the number of connections used in the attack. DoS attacks can target more than one site or system at a time. An attack becomes a distributed denial-of-service, referred to as ‘DDoS’, when it comes from multiple computers (or vectors) instead of just one. This is the most common form of DoS attack on websites.
How does a DDoS attack work?
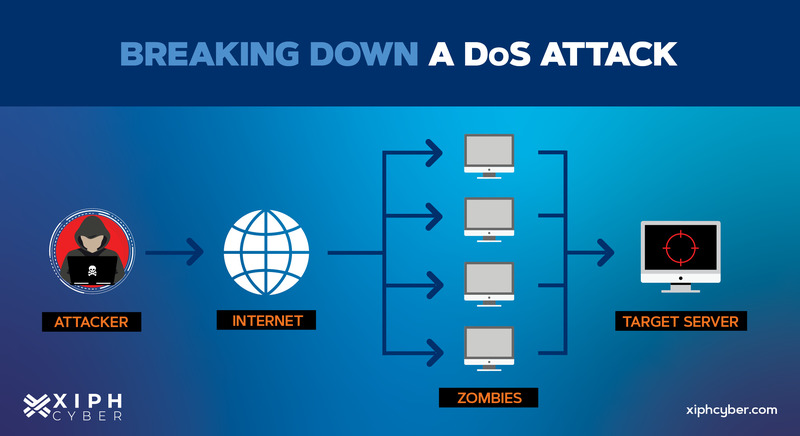
DDoS attacks distribute malicious traffic through a network of internet-connected machines or a botnet. Hackers can create a botnet by compromising a network of internet-connected devices with malware or by purchasing one on the dark web. Once a botnet is established, the attacker can direct an attack by sending remote instructions to each bot. When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial of service to normal users.
Tell-tale signs of a DoS attack
Generally, the best way to examine a potential DoS attack is through traffic analytics tools. DoS attacks are hard to discern as they often resemble common network connectivity errors or excess bandwidth usage. Some tell-tale signs of a DoS attack include:
- Slow network performance such as long load times for files or websites
- A network suddenly can't connect to the internet, or a website does not load
- A sudden loss of connectivity across devices on the same network.
What type of businesses do DoS attacks affect?
Large-scale DoS attacks on multinational conglomerates or large corporations are well reported. Some of the most famous DDoS attacks have impacted big names like Google, Amazon Web Services, GitHub, and more.
But DoS attacks can also target smaller businesses and just about any aspect of an online business including emails, online accounts, e-commerce sites, and websites. In fact, hackers are beginning to turn their attention to smaller enterprises that they see as easier targets ─ unlikely to have sophisticated DoS mitigation and cyber security protocols in place. Small businesses without protection are particularly vulnerable to DoS attacks.
According to the Cisco Annual Internet Report (2018–2023) White Paper, DDoS attacks are on the rise and will double to 15.4 million by 2023 globally.
Why do DoS attacks happen?
Hackers can launch a DoS attack on a business or organisation for a multitude of reasons, most commonly to make ransom demands, while businesses themselves are also known to launch DoS attacks on their competitors to disrupt their operations. The thinking is that if a competitor’s website is down, all the traffic will come to your website instead. DoS attacks can cause a significant loss in revenue, particularly for online retailers, and result in further reputational damage.
Although, DoS attacks aren’t always about extorting money and undercutting the competition. Hacktivists also use DoS attacks to make topical or political statements, strongly voice an opinion or show support or opposition to a topic or activity. Famous examples include DoS attacks on the Church of Scientology, PayPal, Mastercard, and Visa.
DDoS attacks can also happen between countries or governments. Both political and apolitical hackers can target individual government websites to further their own views and interests, meanwhile, state actors and political parties often attack each other using the DDoS method.
What are the different types of DoS attacks?
Denial-of-service (DoS) is a broad class of cyber attack that disrupts online services and resources by overwhelming them with traffic. DoS attacks typically fall within one of three categories:
- Application layer attack: Targets specific vulnerabilities or programming errors in an application (typically a web server) to cause a denial of service to users. An application layer attack is achieved using different bots/machines to send numerous application requests to the server, eventually overwhelming it. The most common application layer attacks are the HTTP flood attacks in which malicious actors just keep sending various HTTP requests to a server using different IP addresses.
- Protocol attack: Aims to exhaust the resources of a server or network systems like firewalls, routing engines, or load balancers. Examples of protocol attacks include SYN floods, fragmented packet attacks, Ping of Death, Smurf DDoS, and more.
- Volumetric attack: Sends high amounts of traffic, or request packets to a targeted network to overwhelm its bandwidth capabilities. The most common example of a volumetric attack is the DNS amplification attack.
How to prevent DoS attacks
The best way to mitigate DoS attacks is with a multi-layered cyber security strategy that includes both intrusion prevention and threat management systems. Some common ones include anti-spam software, content filtering, using a Virtual Private Network (VPN) gateway to hide your IP address from hackers, web application firewalls to detect malicious requests, load balancers to spread website traffic across multiple servers, and security layers to spot and block attacks before they overwhelm your network. It's also important to have the capacity to scale up bandwidth and server capacity to absorb and mitigate DoS attacks. Most website hosting providers offer unlimited bandwidth for that reason.
How to stop DoS attacks
DoS mitigation requires a tailored approach specific to each business, IT infrastructure, and needs. Most solutions will involve a combination of anti-spam software, data backups, web application firewalls, and various other security layers to prevent DoS attacks. For more information, contact us via email: enquiries@xiphcyber.com.
Posted in: Security