Published Jan 25, 2023 by Xiph
Just like playing Monopoly can teach you about investing without risking your own money ─ penetration testing simulates a cyber attack on your business’ IT infrastructure to help you avoid or better prepare for real cyber threats.

What is penetration testing?
A penetration test ─ also known as a pen test or ethical hacking ─ is a proactive security measure that simulates a cyber attack on your computer systems or networks to identify exploitable vulnerabilities before any malicious actors do. Pen testing should form part of a holistic cyber security strategy.
How does penetration testing work?
Penetration testing is typically carried out by an IT expert or ethical hackers (yes, they exist) who use or mimic the same methods and strategies that real hackers employ to identify your organisation’s ‘hackability’ and adherence to compliance regulations. Penetration testing will simulate various cyber attacks on your computer systems, networks, and web applications.
Penetration testers scale planned attacks using the same tools, techniques, and processes as real hackers to simulate authorised attacks on your IT infrastructure. The purpose of pen testing is to identify weak spots and security vulnerabilities in your systems that need to be patched up, instead of leaving the door open to real malicious actors. Penetration testing would be akin to a bank hiring a fake robber to try to break into the building to access the vault.
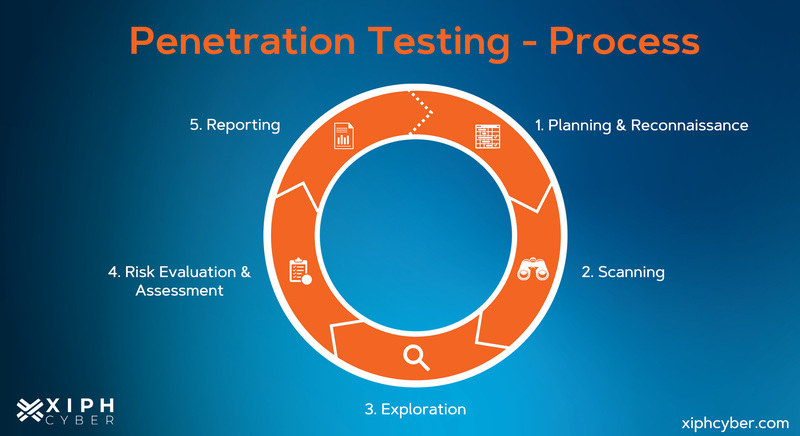
What are the stages of penetration testing?
The pen testing process is typically done in five stages, including:
- Planning & reconnaissance: Gather data and information about the target (i.e. network and domain names, mail server, etc.) to inform the attack strategy. This phase helps pen testers define the scope and goals of the test and map out the attack surface and possible vulnerabilities.
- Scanning: Pen testers use various tools to examine the target’s entire IT infrastructure and how it may respond to various intrusion attempts. This stage scans for vulnerabilities such as bugs in the code, application security issues, and open-source vulnerabilities. Ethical hackers often use a vulnerability scanner to conduct a complete inventory of the security risks posed by identified vulnerabilities.
- Gaining access: This stage is where pen testers try to exploit entry points and flaws identified in your network, applications, and data to gain access. Attack vectors will include web application attacks such as cross-site scripting or SQL injection, network attacks, memory-based attacks, or social engineering (i.e. phishing) to exploit vulnerabilities.
- Maintaining access: The goal of this stage is to see if the vulnerability can be exploited for long enough to achieve the desired malicious action or intent, which may include extrapolating data, executing malicious applications, etc.
- Analysis & reporting: The results of the penetration test are compiled into a report detailing which vulnerabilities were identified and exploited, how long pen testers were able to remain in your systems undetected, and which sensitive data was accessed/compromised.
What happens after penetration testing?
Once penetration testing is complete, your ethical hacker(s) will summarise the results of the assessment into a comprehensive report to share with your IT teams and relevant stakeholders. The report will list vulnerabilities discovered during the test, risk rankings, and recommendations for security controls/upgrades to implement in order of most critical to least.
What are the types of pen tests?
The methodology of penetration testing is split into three types of testing: white box assessment, black box assessment, and grey box assessment.
- White box pen test: The pen tester will be provided with full network and system information before undertaking the pen test. This will include information about source code, network maps, credentials, etc. This is the fastest and most cost-effective option for small businesses.
- Black box pen test: This follows the approach of an unprivileged attacker which means the pen tester is given no prior or internal knowledge of the target system. The tester is not granted any access to the applications or networks. This is the longest process as it involves both reconnaissance and penetration.
- Grey box pen test: This is a combination of white box and black box testing techniques. The pen tester will be provided only limited or selective information about the target organisation’s IT and staffing structure. Testing speed is often quicker in grey box testing since the tester starts with some information.
Penetration testing can be conducted with or without the knowledge of internal teams or your IT and security teams. This is known as covert pen testing and is commonly commissioned by companies that deal in sensitive data like financial institutions. If your organisation is undertaking covert penetration testing, make sure to provide your ethical hacker(s) with the full scope of the assessment and expectations in writing to avoid running into trouble. Penetration testing can be carried out on both external systems like websites and servers and internal systems like emails, software, etc.
Why is penetration testing important for business?
Penetration testing is a vital component of any business’ cyber security strategy as it offers invaluable insights into the ‘hackability’ of your computer systems, applications, wider network and even of your teams. Pen testing evaluates your cyber defences from a hacker's perspective. It’s designed to identify vulnerabilities and remediate weak points before they’re exploited by cyber criminals.
How often should penetration testing be conducted?
Most security experts advise businesses to conduct some form of pen testing at least yearly to ensure consistent IT and network security management and detect emerging vulnerabilities, such as zero-day threats. However, the frequency of penetration testing will depend on your organisation’s size, budget, and the industry it operates within. For example, banking and healthcare industries are required to conduct mandatory penetration testing more frequently than sectors like resources, tech, or retail.
Penetration testing vs vulnerability assessment
A vulnerability assessment often includes a penetration testing component, but these two concepts are distinctively different. A vulnerability assessment provides a high-level overview of potential vulnerabilities and known exposures, mostly using automated tools. On the flip side, a penetration test is more hands-on and accurate as it’s carried out by certified ethical hackers that simulate an attack on your systems, applications, or IT environments to showcase how those security gaps can be exploited in a real-world scenario.
Read more: Vulnerability assessments for businesses
A final word
Not all penetration testing is created equal which is why it’s important to hire a reputable team to undertake pen testing. Our security consultants use a combination of manual and automated techniques to identify potential security issues before they materialise, plus provide a full audit and risk score. For more information, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


