Published Mar 29, 2023 by Xiph
More than 300 billion emails are sent and received daily worldwide – it’s no wonder email accounts are a common target for hackers. Business email compromise attacks can be severe and lead to huge data losses, and reputational damage. Here’s how to protect your email security.

What is email security?
Email security is a catchall term for the practices and technologies that protect email accounts and communications from unauthorised access, loss, or compromise. Common email security tools and protocols include email encryption, secure email gateway filters, spam filters, and multi-factor authentication (MFA), just to name a few.
As email became foundational to business communications and IT operations, cyber criminals continue to find new ways of using email to breach corporate security. The shift to cloud-based email like Gmail and other hybrid email platforms offers several benefits like redundancy, scale and integration, but they also come with risks because their security is outsourced to third-party vendors, and you don’t get a detailed log of incidents or vulnerabilities.
What’s more, email at its core is not very secure because content and communications are not encrypted by default and can be easily used to exploit human error − all it takes is one seemingly innocent click on a link or attachment and your organisation could be exposed.
Cyber criminals often target email accounts to gain an easy entry point to other accounts and devices, and even entire networks. Cyber criminals who know your email address could use phishing, spam, or hijack your personal or business email accounts to gain access to sensitive information, commit fraud or steal your identity. Email is also used to spread malware, spam, and phishing attacks.
How does email security work?
Email security basically inspects incoming emails for malicious threats and encrypts outbound email traffic to protect corporate inboxes, data, users, and organisations more broadly from breaches. For example, most cloud-based email providers feature built-in end-to-end encryption, backup capabilities, customisable spam filters, and other technologies that work together to protect everyone within an organisation that uses email.
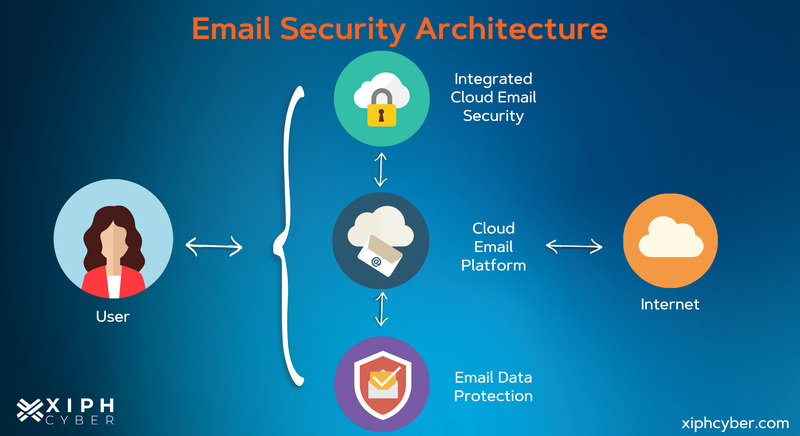.jpg)
Types of email threats to watch out for
While email threats are constantly evolving, they generally fall within these main categories:
Phishing
Phishing is a form of email fraud where hackers trick users into disclosing sensitive information such as login credentials, personal details, and other types of valuable data by sending them an email pretending to be a trusted person, or organisation. Phishing emails may also include a malicious link or attachment.
Read more: Running phishing tests for businesses – best practices & tips
Email spoofing
Spoofing is similar to phishing, but where spoofers go one step further by fabricating email headers and templates to impersonate a trusted person or organisation and trick victims into divulging sensitive information.
Spam emails
This is when email users receive unsolicited, irrelevant, and spammy messages or emails in bulk. These are usually poorly worded and structured. Spammers use spambots to crawl the internet looking for email addresses that are used to create email distribution lists. Spam can also massively impact productivity if left unchecked.
Ransomware
This type of common cyber threat typically comes in the form of a hyperlink sent in a phishing email, which then uses malicious software to block or encrypt target files or corporate data. Hackers will then demand a ransom in exchange for the files or decryption keys.
Read more: How to avoid & deal with a ransomware attack
Data exfiltration
Data exfiltration is the unauthorised data tampering from an email system or network. Hackers can easily gain access to calendars, databases, documents, and images sitting in email systems. Email gateways help your businesses avoid data breaches.
Read more: Network security for businesses
How to ensure email security
Every business should have an email security plan in place that includes the following tools and protocols:
Spam filters: These algorithms scan all incoming emails in real-time and block unsolicited or infected emails from making it into your inboxes.
End-to-end email encryption: This ensures that email communications are encrypted by the sender, and only the intended recipient can decrypt it. Email providers including Google and Microsoft use Transport Layer Security (TLS) encryption to secure emails when in transit over the internet.
Secure email gateway (SEG): This acts as a firewall and inspection point between outsider and business email accounts. SEGs monitor and filter emails from a corporate email server, according to settings set by an IT administrator. They can detect and block malware, spam, and phishing attempts.
Antivirus protection: Antivirus software that can screen emails and attachments for viruses and raise the alarm if anything suspicious is detected before it’s too late.
Multi-factor authentication (MFA): MFA protects your email accounts by requiring users to provide multiple methods of authentication before they can log in, not just a password.
Employee education: Employees should get regular training on how to spot, report and avoid social engineering and phishing attempts, and other attacks executed using email.
How to check your email security
To make your email account more secure make sure to turn on MFA to prevent unauthorised access, update your recovery phone number and email address so that you can get updates of suspicious activity on your account, and always keep your browser, software, and apps up to date. You may also want to turn off access to apps that use less secure sign-in technology, and regularly audit your email activity to see if there’s anything unfamiliar or suspicious. However, in some cases, you may not realise that your email account has been compromised until one of your contacts flags suspicious emails coming from your account.
A final word
Keeping existing and emerging email threats at bay requires a multi-layered approach and superimposing various technologies like cloud-based solutions, spam filters, SEGs, data and recovery, and more. Proactively reviewing your email account’s security will also prevent compromise and help you regain control should it be compromised. For more information on how to keep your email accounts secure, contact us via email: enquiries@xiphcyber.com.
Posted in: Security