Published May 17, 2024 by Xiph
The key to effective cyber security is always to stay one step ahead of malicious actors. One innovative tool that has gained prominence in recent years is the honeypot. This unassuming decoy system is a powerful tool to detect, analyse, and mitigate cyber threats.

What is a honeypot?
A honeypot is a type of deception technology strategically designed to simulate a vulnerable target within a network and lure in cyber attackers. In other words, it’s a digital honeytrap or bait to attract hackers and get invaluable insights into their methods. The purpose of a honeypot is to divert and contain malicious activity to allow cyber security teams to study potential threats' tactics, techniques, and procedures (TTPs), as you would in a sandbox environment.
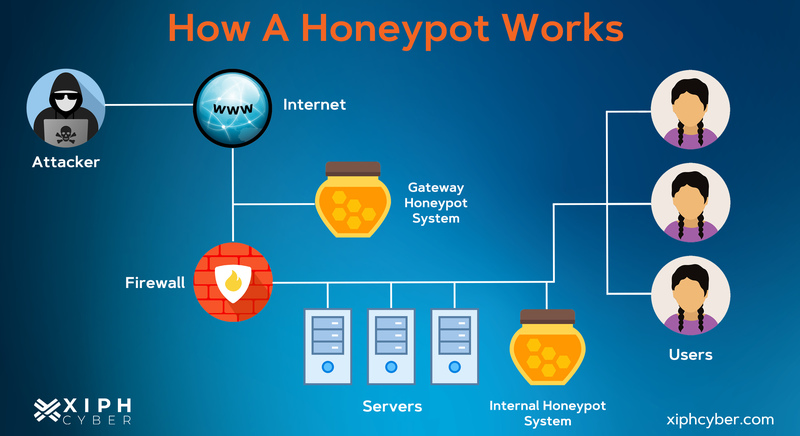
How does a honeypot work?
Honeypots mimic genuine network resources or services, such as a web server, database, or email server. These decoy systems appear enticing to potential attackers drawn to exploit perceived vulnerabilities. Once an intruder interacts with the honeypot, their actions are meticulously monitored and logged for analysis. They pose no risk to your actual systems or legitimate users.
Honeypots don’t always have a single decoy system but can have multiple (called a honeynet) and be paired with other resources like firewalls, routers, and monitoring tools. A honeynet looks like a real network and contains multiple systems hosted on one or only a few servers, each representing one environment. For example, you could deploy a honeynet to represent different operating systems in your organisation.
Production vs research honeypots
There are two primary types of honeypot designs – production and research honeypots.
-
Production honeypots: These are deployed within an organisation's network infrastructure to identify and deflect real-world threats. They are designed to resemble legitimate systems and have sophisticated detection mechanisms.
-
Research honeypots: These are intentionally left more vulnerable to encourage extended interaction. Their primary objective is to gather extensive data on cyber threats, often at the expense of being more high-interaction and potentially risky.
Types of honeypots explained
1. Pure honeypots
Pure honeypots are standalone systems with no genuine production value. They exist solely to attract malicious activity and are not connected to any critical infrastructure. The information gathered from pure honeypots is invaluable for understanding emerging threats and attack techniques.
2. High-interaction honeypots
High-interaction honeypots provide a comprehensive and realistic environment for attackers to explore. They replicate actual operating systems and services, enabling in-depth analysis of attacker behaviour. However, they are resource-intensive to set up and often require additional technologies like virtual machines to ensure attackers can’t access the real system.
3. Low-interaction honeypots
Low-interaction honeypots offer a more controlled environment, emulating only specific services or protocols. While less resource-intensive than high-interaction honeypots, they provide limited insights into attacker behaviour and can collect data from blind attacks such as botnets and malware.
Honeypots & the types of activities they detect
There are several types of specialised honeypot technologies, including:
Malware honeypots
These honeypots are designed to attract malware and serve as bait for cyber criminals seeking to distribute or deploy malicious software. They capture samples for analysis to better inform cyber security protocols.
Spam honeypots
These honeypots capture spam emails and the associated infrastructure used in email-based attacks. Organisations can enhance their email security measures by identifying the sources of spam.
Database honeypots
Database honeypots mimic database servers, enticing attackers seeking to exfiltrate sensitive information. They monitor for suspicious queries and unauthorised access attempts, safeguarding critical data.
Client honeypots
Client honeypots masquerade as vulnerable systems waiting to be attacked by malicious servers. They help uncover malicious servers and the tactics employed to compromise client-side applications like web browsers or login pages.
Benefits & disadvantages of using a cyber security honeypot
Benefits of honeypots
Threat intelligence: Honeypots offer invaluable insights into emerging threats and enable proactive defence strategies.
Incident response: Honeypots facilitate early detection and swift response to potential cyber threats to minimise damage.
Attack surface reduction: Honeypots divert attackers from critical infrastructure to help protect vital systems and data.
Honeypot disadvantages
Resource intensive: High-interaction honeypots demand significant IT and human resources to set up and maintain.
False positives: Honeypots may inadvertently trigger false alarms from benign automated scanning or research activities.
Honeypot limitations
While honeypots are an effective tool in a cyber security arsenal, they have limitations. They are designed to complement, not replace, existing security measures. Honeypots alone can’t provide comprehensive protection against all types of cyber threats, and their effectiveness is only as good as the security teams who configure and monitor them.
A final word on honeypots
Honeypots play a crucial role in modern cyber security as they offer a proactive means of threat detection and intelligence gathering. By understanding their types, benefits, and limitations, organisations can leverage honeypots effectively to bolster their cyber security posture and stay ahead of evolving cyber threats. For more information on how to deploy honeypots within your network, contact us at enquiries@xiphcyber.com.
Posted in: Security


