Published May 13, 2022 by Xiph
Proxy servers provide a valuable layer of protection to your computers and networks. They act as an intermediary between your servers and the internet to help anonymise your web traffic, control internet usage within your organisation, and increase your internet speed. ‘Proxies’ can be set up as web filters or firewalls (or both), to protect your business and network from cyber threats like malware and ransomware. Here’s everything you need to know about proxy servers.

What is a proxy server?
A proxy server is a system or router that acts as a go-between for your network and the internet. This type of firewall is often referred to as an ‘intermediary’ because it sits between end-users (that’s you) and the web pages they browse. A proxy server helps prevent cyber attackers from entering a private network. How? All requests to the internet go to the proxy server first, which evaluates the request and forwards it to the internet. Likewise, responses come back to the proxy server and then to the user. Proxies can be hardware or software.
.jpg)
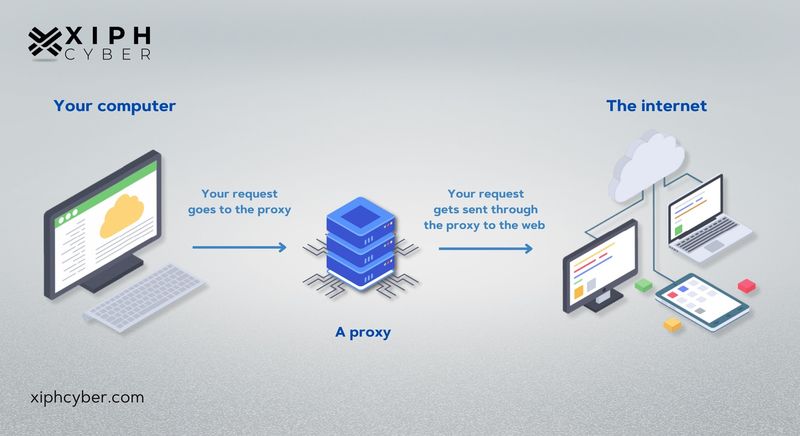
How does a proxy server work?
A proxy server performs the function of a firewall and filter. Because a proxy server has its own IP address that your computer knows, any request you send to the internet goes to the proxy server first, which makes your web request on your behalf, collects the response from the web server, and forwards the web page information to your computer’s browser, like Google Chrome or Safari, for example. A proxy server can change your IP (Internet Protocol) address and encrypt your data before it sends our web request to the web.
Here's a simpler explanation of how a proxy server configuration works:
- You enter a website's URL into your browser
- The proxy server receives your request
- It forwards your request to the web server
- The web server sends a response (website data) back to the proxy server
- The proxy server forwards you the response – the web page.
How does a proxy server protect against cyber threats?
A proxy server adds a layer of security between your servers and the internet to help prevent hackers from entering your private network. It works to essentially anonymise your internet browsing and traffic – a proxy server modifies and encrypts your data (to make it indecipherable), including your IP address, before sending it to the web server. This means the destination server doesn’t know who actually made the original request, which helps keeps your personal information and browsing habits more private. A proxy server can block access to certain web pages, based on IP address or pre-defined rules.
8 types of common proxy servers
Here are the most common and widely used types of proxy servers:
1. Forward proxy: It’s the most common type of proxy and allows multiple clients (you or your business) on a private network to route traffic to an external network like the internet. For example, most businesses use a forward proxy that routes and filters employee traffic to the internet.
2. Reverse proxy: On the other hand, a reverse proxy is used to protect web servers. It accepts web requests from clients (you or your business), forwards the requests to a server that can fulfill them, and returns the server's response to the clients.
3. Dedicated proxy: This is a specific type of private proxy that can’t be shared by multiple clients at the same time. A dedicated proxy is assigned only to one user and can only connect and send web requests from that one client.
4. Transparent proxy: This is the simplest type of proxy. It filters connections between an end-user or device and the internet, without modifying your information or IP address; which is why it’s called a transparent proxy. This means it passes along all of your information, but with the proxy's IP address. The web server receiving the request will know it comes through a proxy.
5. Anonymous proxy: This is an anonymous network connection that simply conceals your network traffic origins by hiding your IP address whenever you surf the internet. Anonymous proxies prevent tracking of your data and information.
6. High anonymity proxy: This is the most secure type of proxy because it doesn’t pass along any information about your private network to web servers. A high anonymity proxy hides your personal/business data, and your IP address and doesn’t identify itself as a proxy when making requests. It gives you the highest level of anonymity possible.
7. Distorting proxy: This works similarly to an anonymous proxy except that it passes along a purposely false IP address. It identifies itself as a proxy and uses that false IP address to submit web requests on your behalf.
8. Residential proxy: This uses a real IP address provided by an Internet Service Provider (ISP) and allows you to browse the internet as a real user in your area, city, or country. This helps legitimise your web requests because they look like regular clients to servers.
Firewall vs proxy server: what’s the difference?
A firewall and a proxy server both form part of your network's security. While a firewall filters incoming and outgoing traffic to your network and blocks unauthorised access to your computers, a proxy server acts as an intermediate between your network and the internet and makes web requests on your behalf. This effectively hides your internal network from the internet.
Do businesses need proxy servers?
Proxy servers should absolutely be part of any business’ cyber security arsenal. They can help prevent data breaches while receiving any data and information you need to run your business. When you use a proxy server, the websites you visit or search for never see your actual IP address or data, but the proxy address instead. Proxy servers also allow you to bypass content filters, access restricted content, balance web traffic, limit internet access in the workplace, and can even increase your connection speeds.
A final word
Proxy servers are an essential cyber security measure for businesses and organisations that connect to the internet or that conduct their operations online in one way or another. For advice or information on the best proxy server solutions, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


