Published Feb 02, 2023 by Xiph
Single sign-on (SSO) makes it easy for your employees to access all their applications with only one username and password instead of dozens – but how secure is it?

What is single sign-on?
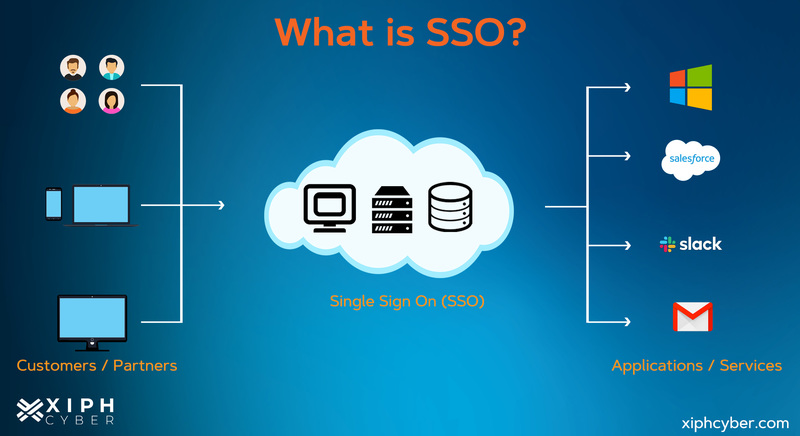
Single sign-on (SSO) is an identity access management tool that combines several application login screens into one. This allows users to access multiple accounts and SaaS applications like Gmail, Slack, and Salesforce by entering only one login, one username, and one password. SSO simplifies username and password management for both users and administrators. It removes the need for users to track different sets of credentials, who instead just remember a single more complex password. This in turn streamlines workflow and adds a layer of safety by reducing the possibility of error. For example, without SSO, a business employee who typically signs into five applications during the workday would need to go through five login routines which then multiplies the possibility of mistakes and not to mention wastes time.
SSO is built on the concept of federated identity ─ the sharing of identity attributes across trusted but autonomous systems. This comes with a major security risk though, for example, if a hacker gained access to one of your team’s credentials which would allow them to infiltrate every application and system that the user has access to.
How does single sign-on work?
Adding SSO to your work environment allows employees to log into one application and automatically be signed into other programs, regardless of the platform, technology, or domain they’re using. SSO creates an authentication token that verifies and remembers all users signed in with their SSO logins. When a user begins a session and signs into a service with their SSO login, an authentication token ─ a piece of digital information ─ is created and stored either in their browser or in the SSO solution’s servers. Any app or website the user accesses after will check with the SSO service for the user’s token to confirm their identity and provide them with access. If the user isn’t signed in, they will be prompted to do so through the SSO service.
SSO technology has various login/access methods, and system configurations available that allow businesses and organisations to choose an SSO system that best suits their needs and allows for suitable modifications. However, SSO is not fit for all industries and sectors, as some organisations will require additional authentication factors such as banks and healthcare providers.
Pros & cons of single sign-on
Advantages of SSO
- Simplifies password management: SSO reduces password fatigue by eliminating the need for users to remember different passwords for every account and web application. Remembering one password instead of many also improves workflow and incentivises users to come up with stronger passwords.
- Improves identity & data protection: SSO provides a central point of authentication for all users, and therefore reduces possible attack vectors. SSO can also be layered with two-factor authentication (2FA) and multi-factor authentication (MFA). With SSO, IT teams also have better visibility of the apps and programs employees are using.
- Increases sign-on speeds: SSO significantly reduces the amount of time users spend entering and resetting passwords. While this isn’t a huge benefit to some businesses, this time efficiency is especially critical in industries where every minute counts like hospitals, emergency services, and social services providers.
- Reduces help desk requests: SSO alleviates some of the burden from IT help desks, as fewer users would call for help with lost or forgotten passwords ─ saving both time and money.
Disadvantages of SSO
- Requires extra-strong passwords: Users need to generate a more unique and complex password for SSO because if it’s cracked, bad actors can access all your accounts and applications.
- If SSO is down, access to all connected sites is stopped: Users may be denied access to all applications, servers, and network resources that run on the same infrastructure. Be sure to choose an SSO system that’s reliable and has a contingency plan in place.
- SSO poses a risk for multi-user devices: The use of SSO on shared devices and computers increases the risks of cyber intrusion, in the case that a user forgets to log out and another needs to use the device.
- If your SSO is compromised, your linked accounts can be compromised: If a hacker gains access to a user’s login details, they could gain control of all applications and accounts linked to the SSO.
- SSO is not always easy to implement: SSO can only be set up successfully if your business has documentation and service technical catalogs. Getting the right permissions, and configurations for SSO can take time, as well as linking the Identity Provider to the Service Provider. The Identity Provider may ask for additional authentication, such as a one-time password or biometric authentication.
How secure is SSO for businesses?
SSO can help businesses mitigate security risks by reducing attack surfaces as users only log in once each day and only use one set of credentials. Reducing login to one set of credentials improves enterprise security and data compliance. Without SSO, organisations have to store and manage separate login credentials for each user and authentication for each website, program, or application in the system, and maintain their own private database of user credentials. SSO reduces those security risks. Users no longer have to keep track of dozens of passwords and organisations can offload sensitive data to their respective third-party SSO services. The problem, however, is that if a single sign-on is compromised, it becomes a single point of failure (SPOF). Introducing an MFA component would reduce this security risk.
A final word
Configuring and implementing an SSO solution for your business will require thorough planning, including clarifying your organisation’s goals moving forward or scalability and identifying who will be using the SSO and in what capacity, and whether to add another authentication system to cover everyone in the organisation. For more information on the best SSO solutions, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


