Published Apr 26, 2023 by Xiph
It’s crucial for business operations and continuity to have the right people access the right digital resources at the right time and for the right reasons. That’s where identity and access management (IAM) comes in. It follows the principle of least privilege access so that the right job roles (identities) in any organisation get the tools they need to perform their duties without ever compromising on security.

What is IAM?
IAM − short for identity and access management − is a security framework that manages user validation and resource access within an organisation. In other words, it ensures that the right users have appropriate access to web resources like web applications, APIs, databases, software, devices, and hardware (i.e. routers, and servers). It typically combines policies, processes, and technologies to validate and manage the roles and access privileges of individual network users and devices. Users can be employees, customers, partners, or third-party providers.
IAM manages user validation and access to business resources, including:
- How users are identified and the roles they are then assigned
- How users can authenticate their identity
- The correct levels of protection and access for sensitive data, systems, information, and locations
- How, and when data can be moved
- When and how often users must prove their identity
- Adding, removing, and amending users in the IAM system.
How does IAM work?
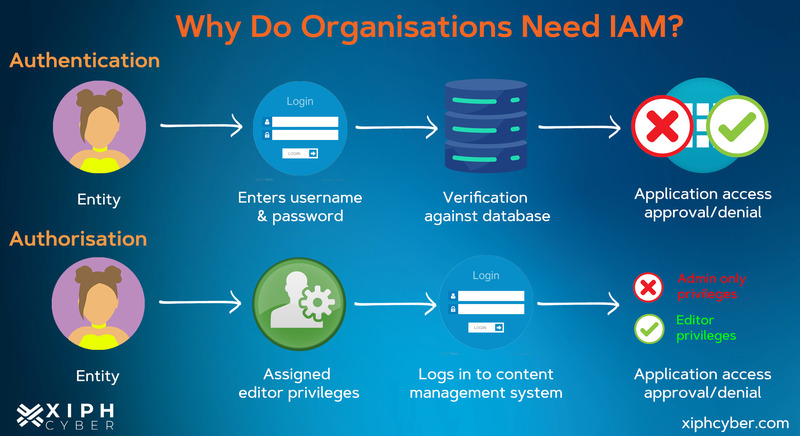
IAM provides a centralised system that allows organisations to create and assign a single digital identity and set access privileges for each user. Digital identities may include a combination of credentials, biometrics, email addresses, PINs, hardware tokens, etc. IAM basically ensures that only authorised users can access and alter enterprise assets. It does so based on two basic concepts: authentication and authorisation.
- Authentication: IAM confirms the identity of a unique user (who they claim to be) by authenticating their credentials against a database. This can be done with single sign-on (SSO), multi-factor authentication (MFA), or risk-based authentication.
- Authorisation: Determines what resources that unique user can access and the level of access they require to do their job based on pre-defined rules. For example, IAM systems may split access privileges for a content management system into an editor, contributor, or admin-only access. Organisations should apply the principle of least privilege and only allow specific users to access and handle sensitive information.
Why do businesses need IAM?
With hybrid working becoming the norm and businesses relying more on users outside of their organisation, IAM is crucial to ensure only the right people have access to internal systems and data. IAM provides a means of administering user access across an entire enterprise and ensures compliance with corporate policies and government regulations. It simplifies identity and access management for businesses and IT teams. It allows businesses to manage user identities by reducing error margins in the process. Traditional security solutions aren’t foolproof, especially those relying only on passwords for authentication.
Suppose an employee’s password was cracked or compromised, along with their recovery email – it would bust the door to your network wide open for cyber criminals. On the other hand, IAM allows users to sign into their portal once where the identification, authentication and authorisation take place simultaneously. Employees no longer have to worry about passwords or their access level to perform their tasks, as IAM gives them access to the precise suite of tools for their job. Permissions can be identity-based (attached directly to users, groups, or roles) or resource-based (attached to web applications or software resources).
Benefits of IAM
IAM simplifies sign-in and user management processes for application owners, end-users, and system administrators which in turn improves business productivity. It helps digital systems and users work together without friction when implemented correctly. Employees can work seamlessly no matter where they are, while centralised management makes sure they only access the specific resources they need for their jobs. And opening systems to customers, contractors, and suppliers can increase efficiency and lower costs.
Common cloud platforms like Microsoft's Azure, Google Cloud, OneLogin and Okta are suitable for employee identity access management in B2C and B2B enterprises, and for developers and security professionals. Modern IAM solutions go beyond simple credential management and include technologies such as machine learning (ML), artificial intelligence (AI), and various algorithms to identify and block suspicious activity.
How can IAM protect business data?
IAM technology implements policies that enforce exactly how users and individual roles within a business can access systems and data, based on an organisation’s specific needs. It can assign specific roles to parts of systems, databases, and information. This means only approved roles can view or amend business data, and that only approved roles can access certain applications and operational systems. Some roles may not be able to send or receive data outside the system, meaning it cannot be exposed to other third parties and applications.
Identity management vs access management: What’s the difference?
While identity management and access management are used interchangeably, they’re not the same thing. Identity management relates to authenticating users or in other words, managing the attributes and roles of each individual user. On the other hand, access management relates to authentication and decides which permissions to grant users based on pre-defined rules and policies.
A final word
There’s no limit to the different approaches for implementing an IAM system. Most solutions available share a similar framework for securing access to digital resources and core features. However, IT teams can build upon existing IAM platforms to implement their own authentication factors and integrations and ensure compliance with industry standards. For more information, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


