Published Aug 03, 2022 by Xiph
The infamous state-sanctioned spyware Pegasus was originally used by governments to track down terrorists and serious criminals. It was reportedly employed by Mexican authorities to capture drug lord Joaquín “El Chapo” Guzmán in 2016. Fast forward a few years and it seems everyone and anyone could be on the hit list.

Reports have confirmed that the very same spying tool is being used to target civilians ‘of interest’, namely activists, journalists, business people, government officials, and even state leaders. Pegasus malware is not only used to spy on ‘high-end’ individuals but also for mass surveillance.
The Pegasus Project, spearheaded by the journalism non-profit Forbidden Stories and Amnesty International revealed a data list of more than 50,000 phone numbers on the NSO Group (the creators of Pegasus) clients’ lists since 2016, although the company says this doesn’t mean numbers were selected for surveillance using Pegasus. However, forensic analysis did find some (not all) phones tied to numbers on the list had been potentially infected by Pegasus.
While state-based surveillance is nothing new, Pegasus is a poignant example of how vulnerable we all are to digital spying and cyber intrusion.
What’s Pegasus spyware?
Pegasus is a hacking software – or spyware – that can infiltrate devices and mobile phones running most versions of iOS and Android. It was developed by Israel-based cybersecurity company NSO Group and licensed to governments and law enforcement agencies around the world to counter terrorism and national security threats. This means any ordinary Joe or average citizen is unlikely to be targeted by government-wielding Pegasus, although this of course doesn’t guarantee privacy.
The earliest versions of Pegasus date as far back as 2016, so the technology is nothing new, however, its capabilities and breadth have expanded significantly since then. NSO Group’s client list now features over 40 countries (and counting), with the company insisting it vets the human rights records of all its foreign government clients. It states that the Pegasus malware “cannot be used to conduct cyber surveillance within the United States, and no foreign customer has ever been granted technology that would enable them to access phones with US numbers.”
While Pegasus is highly sophisticated spyware only sold to vetted foreign governments, it’s only a matter of time before expert cybercriminals create a similar malware for far more sinister purposes.
How does Pegasus hack phones?
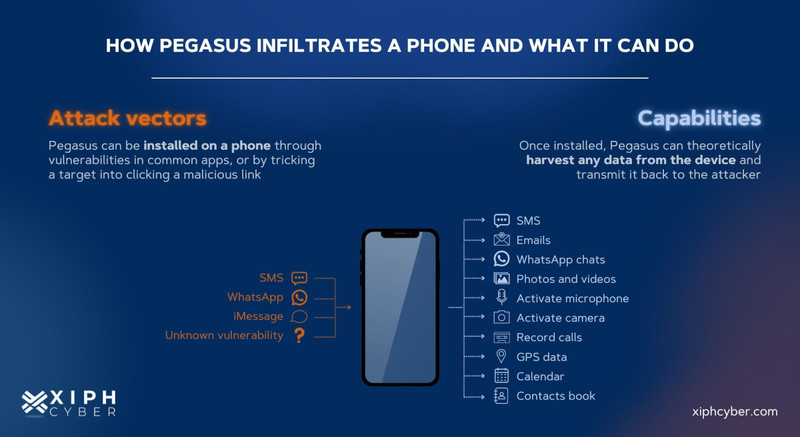
Pegasus spyware can be covertly installed on smartphones by simply exploiting vulnerabilities in commonly used apps, or operating systems or by spear-phishing − tricking a victim into clicking a malicious link or document that secretly installs the spyware. Pegasus can also infiltrate a smartphone just by calling a user via WhatsApp, even if the user doesn’t pick up the call, and can even delete the record of the missed call. Another way is by simply sending a message to a user’s phone that produces no notification. Pegasus doesn’t require any user action or input to infect a device. This is known as zero-click spyware.
On Android devices, Pegasus doesn’t rely on zero-day vulnerabilities but instead uses a well-known rooting method called Framaroot, which leaves the targeted user unable to detect any issues. For iOS devices, it can simply jailbreak the device and exploit zero-day vulnerabilities.
Once installed, Pegasus can turn any Android or iOS smartphone into a fully-fledged surveillance device. It can access and harvest any data from a device including SMS messages, emails, WhatsApp messages, iMessages, and other written communications. It can record incoming and outgoing calls, web searches, passwords, location history, and steal photos and videos. Pegasus also has the ability to activate cameras and microphones to spy on victims in real-time.
Protecting your smartphone from Pegasus spyware
Unfortunately, zero-click attacks are extremely difficult to prevent, even by those trained to prevent them. However, there are some steps you can take to give your smartphone the best fighting chance against Pegasus spyware:
- Keep your device(s) in a Faraday bag/sleeve when not in use
- Only open links, files, or email attachments from known sources
- Never click suspicious links or links received via SMS
- Disable iMessage, WhatsApp, and other messaging platforms
- Encrypt all of your critical data and information
- Reboot your device daily and always install the latest updates and security patches
- Install strong antivirus software on your device, including one that checks if/when your device is jailbroken
- Always use a Virtual Private Network (VPN) to encrypt traffic
- Avoid using public Wi-Fi; even if you are accessing it with a VPN
- Use strong and hard-to-guess passwords & multi-factor authentication (MFA) for each device
How to check if your smartphone is infected with Pegasus spyware
It would be hard to know for sure if your phone is infected by Pegasus spyware since it’s been purposely designed to evade forensic analysis and detection by antivirus software. However, Amnesty International the Mobile Verification Toolkit (MVT) to help detect traces of Pegasus spyware. Users can also check for tell-tale signs of spyware infection including:
- Inexplicable increases in data usage (typically, data usage is higher in phones infected with spyware), sudden battery drainage
- Sudden or unexplained battery drainage
- Traces of WhatsApp missed calls
- Unknown applications or software running on your device
- Poor and slow performance of your device
- Changes in camera and microphone permissions
- If your phone has been rooted (or jailbroken, in the case of iPhones)
- Device performs poorly
What to do if your phone has been infected by Pegasus spyware?
It would be hard to know for sure if your phone is infected by Pegasus spyware − it’s been purposely designed to evade forensic analysis and detection by antivirus software since it exploits zero-day vulnerabilities that are unknown to the developers of operating systems and antivirus applications. It also has self-destruction features. One way to find out if your phone has been infected with Pegasus spyware or any other malware is to speak to cyber security experts with experience in the field of spyware detection about doing an audit. Alternatively, the only other way to eliminate Pegasus spyware is to change devices entirely, possibly opting for a custom-built secure smartphone like our range of CommuniTake IntactPhones.
A final word
Our phones store our most personal information, including photos, videos, and communications. Spyware can reveal a lot about a person and bypass the encryption that protects our data and privacy. If you’re looking for advice on how to best protect your devices from spyware like Pegasus and others, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


