Published Feb 22, 2023 by Xiph
In our modern world, cyber threats and hacking techniques are aplenty and always evolving, especially ones that can exploit data applications, such as SQL injection attacks.
What’s a SQL injection?
SQL injection ─ SQLi for short ─ is a cyber attack whereby attackers inject a malicious SQL code into a data-driven application or database. SQL stands for Structured Query Language which is used to communicate with a database. This server-side programming language is specially designed for storing and processing information in database management systems. SQL queries execute commands, including commands to retrieve data, update data and delete records.
Hackers can bypass security measures of applications and use SQL queries to modify, add, update, or delete records in a database. SQL injection attacks can often cause a serious data breach and compromise sensitive company data, including financial information, customer details, and personal information. Some SQL injection attacks may even go as far as destroying data systems entirely.
Read more: Common types of malware & how to avoid them
How does a SQL injection work?
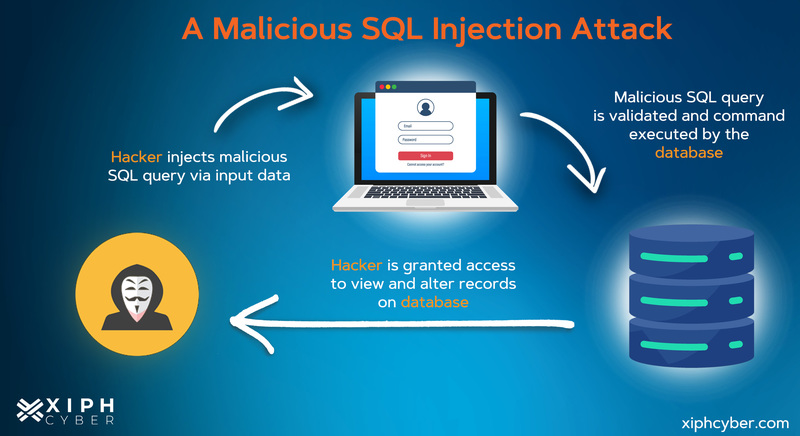
A SQL injection manipulates SQL code/commands to interfere with back-end databases to gain access to protected resources, such as sensitive data. SQL injection attacks alter SQL queries, injecting malicious code by exploiting application vulnerabilities. Successful SQL injection attacks allow attackers to modify database information, access sensitive data, execute admin tasks on the database, and recover files from the system. There are several ways that malicious users can execute an attack, including exploiting vulnerable user inputs that allow free text within a web application or web page. In some cases, attackers can also issue commands to the underlying database operating system. This common attack vector is often used to attack SQL databases, although websites are more frequent targets.
How do SQL injection attacks impact businesses?
SQL injection attacks can severely impact websites or web applications with databases such as MySQL, Oracle, or SQL servers. This can therefore compromise sensitive business data and private customer information. In recent years, various high-profile security breaches have resulted from SQL injection attacks. Companies that have famously been attacked by SQL injection include Target, Yahoo, LinkedIn, Sony Pictures, and 7-Eleven, just to name a few. SQL injection attacks can impact businesses and applications in several ways, including:
- Exposes sensitive business information: Attackers can access, alter, or delete corporate data, risking the exposure of sensitive company information stored on database servers.
- Compromises user/customer privacy: Depending on the data stored on the SQL server, an attack can expose private user data, such as personal information, credit card numbers, etc.
- Compromises administrative access/credentials: Attackers can infiltrate databases storing user credentials and impersonate users with access privileges. To reduce this risk, businesses should create a database with the least possible privileges.
- Compromise systems access: SQL injections can target database servers with operating system privileges and use these permissions to access other sensitive systems. Attackers can use this lateral movement to cause additional damage to sensitive information.
SQL injections are one of the most serious web application security risks, and their impact can be devastating for businesses, so acting accordingly and promoting prevention is the best protection. Organisations should aim to limit vulnerabilities before a SQL injection attack can occur.
Types of SQL injections
SQL injection attacks typically fall within three categories: in-band SQL injection, inferential SQL injection, and out-of-band SQL injection.
- In-band SQL injection: This is the most common type of SQL injection attack and the easiest to exploit. This is when an attacker uses the same communication channel to both launch the attack and gather results. Common techniques include an error-based SQL injection which gives information about the database structure when a SQL command is used to generate an error message from the database server or a union-based SQL injection which uses the UNION SQL operator to combine select statements and return a single HTTP response.
- Inferential SQL injection: Also referred to as a blind SQL injection, this is where data is not actually transferred between a web application and attacker(s). Instead, a malicious user can learn about the structure of the server by sending data payloads and observing the response. There are two kinds of blind SQL injection, Boolean injection, and time-based injection. A Boolean-based SQL injection sends a SQL query to the database, forcing the application to return a different result depending on whether the query is a true or false result. Meanwhile, a time-based SQL injection sends a SQL query to the database which forces the database to wait for a specified amount of time (in seconds) before responding.
- Out-of-band SQL injection: This is the least common type of attack, whereby the attacker(s) use a different communication channel for the attack and for gathering the results. Attackers use this method if a server is too slow or unstable to use inferential SQL injection or in-band SQL injection.
How to protect your business from SQL injection attacks
You can limit your organisation’s exposure to SQL injection attacks by applying tried and tested prevention techniques including:
- Input validation to verify that all types of user-supplied input into data workflows are properly formatted and authorised.
- Using stored procedures to build SQL statements with parameters stored in the database and called from the application.
- Businesses should also use Zero Trust security and the principle of least privilege access (POLP) to users/accounts that connect to SQL databases.
- Limit database accounts across different websites and applications.
- Apply security patches from vendors when available.
Read more: Why your business needs Zero Trust security
A final word
SQL injection is a common hacking technique that can have severe and irreversible consequences, so protecting your business from this cyber threat should be high on your priority list. Businesses should always follow best practices, including Zero Trust security, applying least privilege access, as well as regularly testing for vulnerabilities. For more information or advice on how to reduce your business risk of a SQL injection attack, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


