Published Dec 01, 2022 by Xiph
With most businesses now using cloud solutions to streamline their operations, as well as to store and manage sensitive data, including customer data; cloud services have become attractive targets for hackers. Cloud infrastructures that remain misconfigured or without adequate cloud security protocols in place can put your business and data at risk. We explain why and how below.

What is cloud security?
Cloud security or cloud computing security is a set of policies, controls, procedures, and technologies that protect cloud-based systems and infrastructure, including applications and data stored in cloud environments. Common cloud security measures include encryption, data masking, user and device authentication, data and resource access control, and data privacy protection. Cloud security also ensures your business data and applications are readily available for authorised users on-demand. However, third-party storage of your customer and business data, applications, and software, as well as user access via the internet comes with its own attack vectors and security risks.
What is could computing?
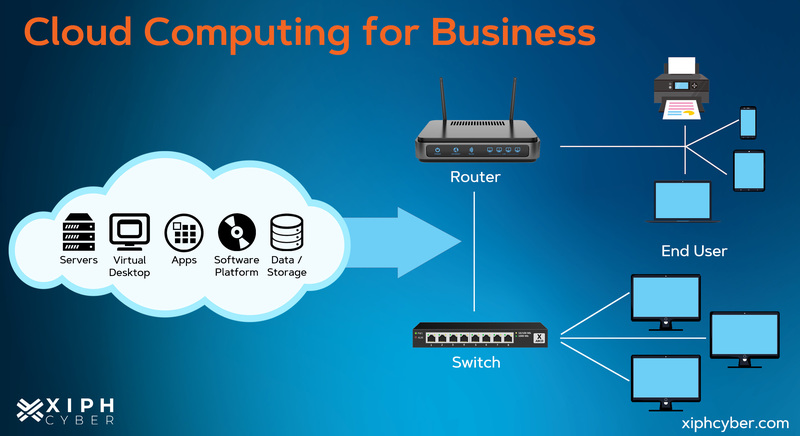
Cloud computing is basically anything that involves delivering computer services over the internet referred to as ‘the cloud’. This includes cloud-based applications, software, servers, storage or databases. Cloud computing is generally delivered via three different models:
- Software as a service (SaaS)
- Infrastructure as a service (IaaS)
- Platform as a service (PaaS).
Most organisations and small and medium-sized enterprises (SMEs) use some type of cloud data storage and cloud SaaS solutions instead of relying on expensive and complex IT infrastructures. The downside to that though is that because so many businesses now depend on cloud services to store and manage sensitive data, including customer and financial data, cloud computing services have become very attractive targets for cyber criminals.
Read more: What is cloud storage & is it safe?
How cloud security works
Cloud security consists of protecting data through data loss prevention measures, and customers' privacy, setting authentication rules for individual users and devices, threat monitoring, detection, and response, business continuity and disaster recovery, regulatory compliance management, and more.
Cloud security can be configured to the exact needs of your business or to different components of cloud systems. For example, web filtering and authenticating access usually go hand in hand. On the flip side, your business’ sales team should always be able to access customer data, but not the marketing or design team. Your customers’ financial information should be strictly guarded and encrypted.
Read more: What is encryption & how does it protect your data?
Cloud security is the shared responsibility of both your cloud service provider and your organisation. Typically, the cloud provider is responsible for the security of hardware and software, while business operators are responsible for the security of their own assets, including virtual machines, applications, and data.
Why is cloud security important?
Cloud security ensures your organisation’s data security, regulatory compliance and continuity. Cloud environments house multiple client infrastructures under the same umbrella (i.e. servers) which can be compromised by malware or hackers. In fact, misconfigured assets account for most breaches of cloud computing environments.
By default, most cloud providers follow best security practices to protect the integrity of their servers. But businesses have the responsibility to protect their own data, applications, and workloads running on the cloud. Without taking active steps to improve their cloud security, organisations can face significant governance and compliance risks when managing client information, regardless of where it’s stored and managed.
5 top security issues with cloud computing
Here are the most common risks and challenges that come with using cloud computing services:
- Unauthorised access: Most cloud security threats with PaaS and SaaS solutions can be linked to identity and access management (IAM) issues. Cloud-based deployments and application programming interfaces (APIs) outside the network perimeter are directly accessible remotely either using public Wi-Fi or personal devices. While accessibility of this infrastructure to employees and customers is a necessity for many businesses, it also makes it easier for outsiders to gain unauthorised access to an organisation’s cloud-based resources and data.
- Unsecure APIs & interfaces: Cloud service providers offer a number of APIs and interfaces for their business customers to use which are essentially a front door to the cloud. Organisations must be diligent in managing, monitoring and securing their interfaces and APIs. Misconfigurations of cloud security settings are a leading cause of cloud data breaches. The security of any cloud service starts with how well these are safeguarded and is the responsibility of both your organisation and third-party cloud service provider.
- Reduced visibility & control: Cloud-based resources are located outside of the corporate network and operate on infrastructure provided by third-party cloud services. As a result, many traditional tools for achieving network visibility are not effective for cloud environments, and some businesses lack cloud-focused security tools. This can limit an enterprise’s ability to monitor its cloud-based resources and protect them against cyber attacks.
- System vulnerabilities: Cloud APIs and environments are inherently prone to system vulnerabilities because they’re built on complex infrastructure and managed outside of your business by third-party providers. Unsecure operating systems and shared storage/resources are just some system vulnerabilities hackers can use as gateways into your network and for data theft.
- Data breaches & losses: Cloud-based environments make it easy to share data across teams and remote working environments and can be accessed directly from the public internet. The ease of data sharing in the cloud is both a major asset to collaboration in the cloud and a cyber security threat.
The basic components of cloud security
A cloud security plan for your business should focus on three basic principles:
- Identifying sensitive data, cloud usage state and associated risks
- Setting up protections for your cloud infrastructure
- Having a robust response plan in the event of an attack.
Cloud security should always start at the lowest possible practical level, and as close to the data storage location as possible. The challenge in this, however, is not solely about implementing security and maintaining data privacy, but also about implementing consistent controls and policies.
In practice, businesses should always regularly monitor their systems and cloud services for potential vulnerabilities and be on the lookout of unusual activity that may indicate a cyber threat.
Best cloud security solutions for businesses
Cloud security should be tailored specifically to your business needs and regulatory obligations and will therefore be dependent on several variables. However, there are common cloud security solutions every business needs to establish a secure and sustainable cloud computing network. These include:
Data protection & data loss prevention (DLP): Ensures your cloud data is always encrypted both at rest and in transit. DLP services are designed to ensure the security of regulated cloud data. It monitors and analyses who can access your business and sensitive data and how it’s being shared. DLP solutions use a combination of remediation alerts, data encryption, and other preventative measures to protect all data stored on the cloud.
Identity & access management (IAM): This framework of policies and technologies ensures that only authorised users get access to both on-premises and cloud-based services and resources. The core functionality of IAM is to create digital identities for all users within your organisation to actively monitor their activity and apply restriction(s) on sensitive data interactions.
Security information & event management (SIEM): This is a comprehensive security solution that automates threat monitoring, detection, and response in cloud-based environments. This gives you real-time analysis of security alerts generated by software and applications within your cloud network.
Business continuity & disaster recovery: Despite preventative measures businesses can take to secure their cloud-based infrastructures and data, breaches and disruptive outages can still occur. That’s where disaster recovery solutions come in. They’re designed to expedite the recovery of lost data and applications and ensure your business continuity no matter what.
A final word
As mentioned, there is no one-size-fits-all or fail-safe cloud security approach that will 100% protect your cloud environment. What’s more, different businesses will need different cloud security solutions, depending on how much data they need to store, how sensitive that data is, how their existing on-premises infrastructure is configured, which applications they use, and more. For more information, contact us via email: enquiries@xiphcyber.com.
Posted in: Security