Published Nov 10, 2022 by Xiph
Cloud hosting, software-as-a-service (SaaS), and remote working have become the norm, with more servers and devices (endpoints) connecting to business networks than ever before. This gives hackers more access routes to launch an attack on your enterprise.

Endpoint security is often considered the last line of defence to protect networks from intrusion, but it should be one of the first cyber security measures on your wish list. We cover everything you need to know.
What is endpoint security?
Endpoint security is the process of protecting endpoints or entry points of end-user devices like servers, desktops, laptops, and mobile devices (i.e. smartphones, tablets, etc.) from threats. Hackers often target endpoints to gain entry into networks or cloud environments for exploitation and malicious intents. Typically, endpoint security protocols include a combination of firewalls, Virtual Private Network (VPN) gateways, antivirus/malware protection, web filtering, application/patch management, cloud perimeter security, and endpoint encryption.
Read more: Common types of malware & how to avoid them
What's considered an endpoint?
An endpoint is any device that’s physically an endpoint on a network. Some common examples of endpoints include:
- Most IoT devices/systems
- Servers
- Computers
- Laptops
- Tablets
- Smartphones
- Wearables (i.e. smartwatches, fitness trackers, etc.)
- Printers
- Point-of-sale (POS) devices
- ATMs
- Medical devices
- Smart systems (including smart security systems, smart refrigerators, smart door locks, etc.)
How does endpoint security work?
Endpoint security is deployed and operated directly on endpoints to prevent intrusions into your network. This is a cyber security layer applied at the perimeter of your local network (on devices) to trace all incoming connections.
Businesses and organisations usually use some type of Endpoint Protection Platform (EPP) on devices to examine files and data packets that enter the network. Each request, regardless of device or user, is examined for potential cyber threats. EPPs secure endpoints through application control to block the use of applications and files that are unsafe or unauthorised.
The best endpoint security solutions are cloud-based, protect both physical and virtual devices, and use real-time machine learning to continuously monitor and adapt each endpoint’s threat detection, protection, and prevention.
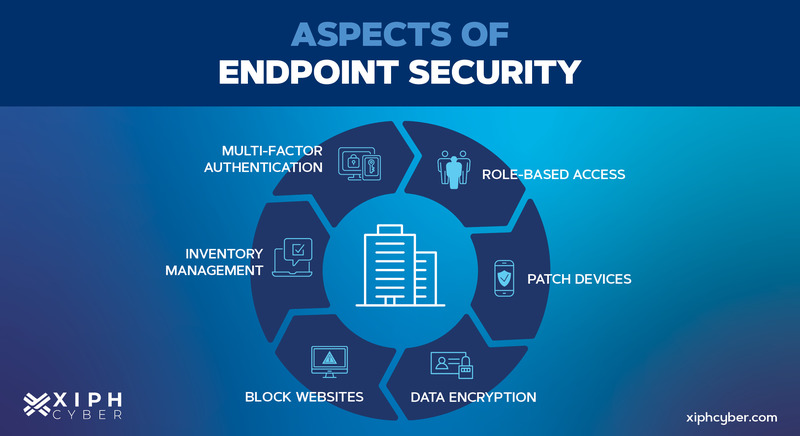
What’s the difference between endpoint security & network security?
Endpoint security is mainly focused on protecting various endpoints and end-user devices like mobiles, PCs, laptops and IoT devices that connect to a corporate network. Meanwhile, network security runs at the network layer to protect data, devices, files and information stored or shared over your business network. An effective cyber security solution employs both endpoint and network security to safeguard corporate networks and are often considered subsets of each other.
Why is endpoint security important?
Endpoint security is a fundamental pillar of cyber security, particularly for businesses to protect all devices and access points on their corporate network. By extension, endpoint security also protects operating systems, customer data, business information, intellectual property, and stakeholders from ransomware, phishing, malware, and other cyber attacks.
Cyber criminals are known to favour endpoints as gateways into corporate and business networks. In fact, a study by the Ponemon Institute found that 68% of organisations have experienced one or more endpoint attacks that successfully compromised their data and/or IT infrastructure.
This means that every device or server an employee uses to connect to any business system or network represents a cyber security risk ─ a potential gateway for cyber criminals into your business. Businesses should remember that security breaches can either come through the network, or via endpoints, which is why it’s important to invest in an integrated suite of endpoint and network protection technologies.
Endpoint protection platforms vs traditional antivirus software
Antivirus software monitors any device it's installed on, and typically scans your systems at scheduled times to detect and prevent known malware threats. On the other hand, an endpoint protection application is much more comprehensive and uses Endpoint Detection and Response (EDR) technology to track and investigate suspicious activity in real-time. In summary, endpoint security solutions cover your entire network, while antivirus software covers a single endpoint and only detects and blocks malicious files.
Does your business have adequate endpoint security?
Many companies have poor endpoint security because they still rely on traditional antivirus defences to protect their network. Antivirus software alone isn’t enough to protect networks against a breach. Antivirus software tend to be reactive not proactive (detect viruses but don’t always prevent malware infection), have a low detection rate, and don’t offer protection against social engineering threats like phishing. That’s why antivirus software should only be used as a supplemental tool in keeping a network secure.
Businesses need advanced endpoint security protections to thwart modern cyber threats, including at the very least endpoint encryption, firewalls, web and email filtering, and backup and disaster recovery solutions.
How to ensure endpoint security
Endpoint security solutions often use a client-server model of protection ─ combining both a centrally managed security layer to protect the network and client software locally installed on each endpoint used to access a network. This is to help detect and prevent known, unknown and zero-day threats delivered through malware, no matter if your end-user devices are online or offline, on-premises or off, connected to your organisation’s network or not. Businesses should use endpoint protection applications that incorporate local and cloud-based threats analysis.
Key features to look out for in endpoint security platforms include endpoint detection and response capabilities, anti-malware and data protection (including backup reminders), reports and alerts to get notifications about updates and vulnerabilities, and incident investigation and remediation.
What our experts recommend: For businesses who want complete protection 24/7 and peace of mind, the Xiph Cyber Security Operations Centre (SOC) uses a combination of analysts and artificial intelligence (A.I) to detect, prevent, inspect and eliminate cyber threats, and also offers incident/breach responses. For purpose-built mobile devices, check out the CommuniTake range ─ expertly engineered to improve the security level of your connected devices.
A final word
Any businesses ─ big or small ─ and in any industry, should prioritise endpoint protection to prevent cyber criminals from infiltrating private and corporate networks through unsecured endpoints. For more information, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


