Published Sep 18, 2023 by Xiph
In today's digital world, the battle for security extends beyond firewalls and encryption protocols. Social engineering continues to emerge as the biggest threat to businesses and individuals. In fact, social engineering attacks account for about 25% of data breaches in small and medium-sized enterprises (SMEs), according to the OAIC.
What is social engineering?
Social engineering or human hacking is a malicious technique cyber criminals use to manipulate individuals into revealing confidential information or performing actions that compromise security. Social engineering preys on human psychology, unlike traditional hacking methods that exploit software vulnerabilities.
The primary goal of social engineering is to breach security protocols or obtain sensitive information, such as login credentials, financial information, or personal identification information like names, addresses or contact details.
How does social engineering work?
Social engineering exploits human error and usually elicits false trust, authority, or fear to trick victims into divulging valuable information. Attackers may even study their targets and gather information from publicly available sources like social media profiles and company websites before launching an attack campaign. Some may even craft convincing scenarios or messages to manipulate their victims.
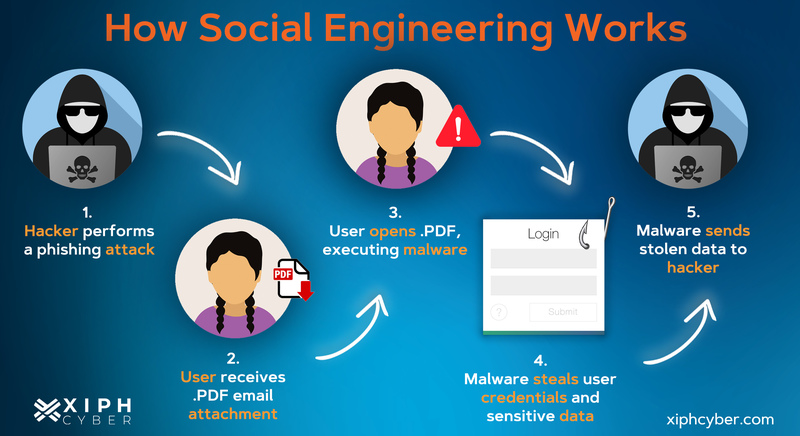
A social engineering attack requires preparation, and cyber criminals often need to conduct some research before launching their deceptive schemes. This reconnaissance phase involves gathering information about potential targets, their roles, habits, and vulnerabilities, allowing attackers to craft convincing scenarios and manipulate human flaws more effectively.
Identify the target(s): Attackers carefully select their targets based on their roles within an organisation or the potential value of the information they possess (e.g. access to internal servers or databases).
Gather information: Cyber criminals collect relevant information about their targets (e.g. email addresses, office location) from publicly available sources like social media profiles (e.g. LinkedIn, Facebook), company websites, and online directories.
Craft a convincing scenario: Attackers construct a believable pretext or scenario tailored to rank-and-file team members or leaders. This could involve impersonating a trusted colleague, superior, client or investor.
Launch attack: Attackers will initiate contact with the target(s) using various communication channels — most commonly email. It can also include unsolicited phone calls or social media messages.
Manipulate the target(s): During the interaction, attackers can employ psychological tactics to manipulate the target's emotions, trust, or curiosity. This manipulation leads the target to reveal sensitive information or perform specific actions like downloading a PDF attachment with malware.
Exploitation: Once the target complies with the attacker's requests, the attacker gains unauthorised access to systems, data, or financial assets.
Social engineering attack techniques
Here are some common social engineering attack techniques and possible scenarios.
Phishing
Phishing attacks use deceptive emails or messages to trick victims into revealing sensitive information such as passwords, credit card details, or login credentials. These emails often appear legitimate and can lead to identity theft or financial fraud. An example could be an employee receiving an email that seems to be from the manager, urgently requesting them to click a link to verify their credentials or account details due to a security breach.
Spear phishing
Spear phishing is a highly targeted form of phishing. Attackers conduct extensive research to create personalised emails that appear to come from trusted sources, like colleagues or managers. These emails are crafted to increase the chances of luring specific individuals into disclosing valuable information or downloading malicious attachments.
Baiting
Tempts victims with malware-disguised files or devices by piquing their curiosity or greed. An example would be strategically labelling a file ‘salary comparison’ on a desktop to trick an employee into clicking the file and installing malware that compromises the entire network.
Pretexting
Pretexting involves attackers fabricating scenarios or pretexts to obtain sensitive information from their targets. Common scenarios include impersonating trusted departments, such as IT support or payroll, and requesting login credentials or personal data to resolve supposed issues.
Scareware
As the name suggests, scareware relies on fear tactics. Victims could encounter pop-up messages or alerts claiming their devices are infected with viruses. To ‘fix’ the issue, victims are urged to download fake anti-virus software or pay for unnecessary services, effectively providing financial information to the attacker.
Tailgating
This physical security breach involves closely following a legitimate person to gain unauthorised access to a secure facility. The attacker typically pretends to have forgotten their access card or to be a contractor and then requests the door be opened. Once inside, they move freely, potentially accessing sensitive areas or information.
Watering hole attack
In a watering hole attack, cyber criminals identify websites frequently visited by their target organisation's employees. They compromise these legitimate websites by injecting malicious code. When employees visit these sites, their devices become infected, allowing attackers to gather sensitive information.
Quid pro quo
Attackers use a ‘something for something’ approach in a quid pro quo attack. They offer something valuable in exchange for sensitive information or access. For example, an attacker might pose as a software vendor offering discounted licenses in return for access to an organisation's internal systems.
How to prevent social engineering attacks
Here are some best practices and cyber security measures to implement and mitigate the risk of social engineering attacks.
Awareness and training: Educate employees and individuals about social engineering tactics like phishing and pretexting. Encourage a culture of scepticism when faced with unsolicited requests for information or actions. Run regular phishing tests and training sessions to keep your organisation on the lookout for potential threats.
Identity verification: Always verify the identity of individuals requesting sensitive information or access. For example, if someone claims to be from IT support, confirm their identity with the IT department before providing any information.
Multi-factor authentication (MFA): Implement strong password protection and MFA wherever possible. This adds an extra layer of security by requiring users to provide multiple methods of authentication before gaining access to accounts or systems.
Cyber security software: Invest in robust anti-virus and anti-malware software to detect and prevent malicious software installations. Keep all software updated and patched to address known vulnerabilities.
Email filtering: Employ email filtering systems that can identify and quarantine phishing and malicious emails. These systems can reduce the likelihood of employees falling victim to phishing attacks.
Data encryption: Implement data encryption to protect sensitive information in transit and at rest. AES 256-bit encryption is the most advanced encryption standard.
A final word
Social engineering exploits human vulnerabilities to deceive victims into revealing information, providing access, or taking actions compromising an organisation’s cyber security. Adopting preventive measures to counter these deceptive tactics is often the best protection. For more information, contact us at enquiries@xiphcyber.com.
Posted in: Security


