Published Mar 22, 2023 by Xiph
Believe it or not, you may already have been a victim of spoofing. For example, have you ever received an email or text message purporting to be from your bank or telco provider, asking you to confirm your credentials by clicking on a link? Just like that, you’ve been spoofed.

What is spoofing?
In the context of cyber security, spoofing is the impersonation of a person, organisation (or brand), or even a website to steal data or money or to spread malware through infected links or attachments. This type of cyber attack makes malicious communications or channels look like they can be trusted because they mimic the look and feel of legitimate organisations (i.e. banks, government, etc.) and by spoofing legitimate brands or businesses. Scammers often use spoofing to bypass network access controls or re-direct traffic to conduct a denial-of-service (DoS) attack, or to execute a larger cyber attack such as a man-in-the-middle (MITM) attack.
How does spoofing work?
Spoofing can be carried out using a number of different communication methods or channels. Email, phone, and SMS are popular spoofing vectors, while spoofing can also come within a phishing attack. Spoofers may employ a combination of tactics to impersonate a legitimate brand/organisation, or even an authority, and trick users into handing over sensitive information or clicking on a malicious link. Every spoofing attack features a certain degree of social engineering.
Types of spoofing attacks
Here are the different types of spoofing attacks and techniques, and how they work. Spoofing can take many forms, and can include:
- Text message spoofing: changes sender details like the phone number and/or contact name for phishing or other fraudulent activities. A fake text cannot be responded to or is blocked.
- Email spoofing: occurs when an attacker purports to be a plausible contact like a bank or business you’ve recently dealt with. Spoofers will typically change the ‘from’ field to match a trusted contact or to imitate the name and email address of a known contact. For example, a spoofed email address may use a zero (0) in place of the letter O, or substitute a lower-case (i) for an upper-case (I). This is called a homograph attack or visual spoofing.
- Website and/or URL spoofing: domain spoofing is when an attacker creates a fake website that looks and feels like an existing or trusted site – often by slightly changing domain names. The goal of these attacks is to have users attempt to log into their accounts, at which point the attacker can record their account credentials or other personal information.
- Caller ID spoofing: uses fake caller IDs or disguises a phone number to one that looks like a public number, with spoofers typically posing as customer support staff to gather personal or financial information.
- GPS spoofing: an attack that overrides a GPS-enabled device's original location to a different physical location from the user. GPS spoofing can be used by online gamers or to redirect navigation systems in vehicles or even planes for more sinister purposes.
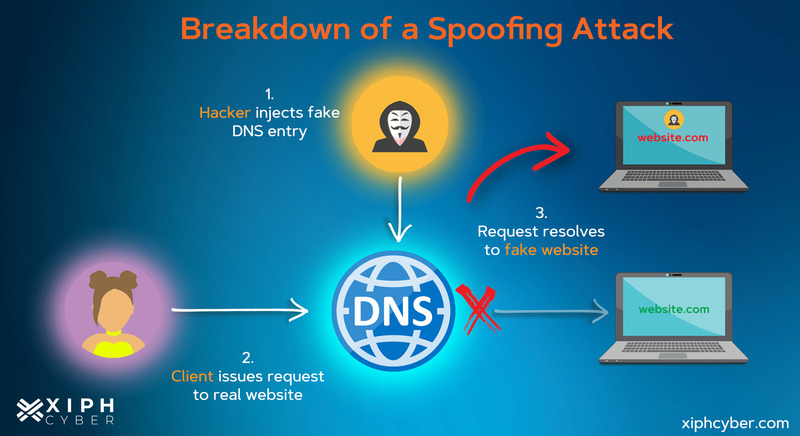
- DNS spoofing: exploits vulnerabilities in a domain name server and redirects traffic to a fake website.
- Man-in-the-middle attack: gets in the middle of internet communications between two targets to intercept or alter data transmitted. MITM attacks are common on public Wi-Fi networks.
- Extension spoofing: occurs when cyber criminals disguise malware in extension folders or files. One common extension spoofing method involves renaming file extensions to ‘docx’ or ‘filename.txt.exe’.
- IP spoofing: also known as IP address spoofing, creates Internet Protocol (IP) packets with a false source IP address to impersonate another computer system.
Spoofing scams in Australia
In Australia, banks, telco providers, courier services like Australia Post, and Government authorities like the Australian Taxation Office (ATO) or myGov are often the main organisations spoofers try to impersonate for their nefarious intents. Victims are more likely to trust any communications that come from official government or industry sources. In the banking space, rival banks NAB, Westpac, and Commonwealth even joined forces on actions to help stop spoofing scams.
How to prevent spoofing attacks
There’s no such thing as zero risk in cyber security, although there are tried-and-tested ways to mitigate the risk of spoofing attacks, including:
- Don’t download or click unsolicited or unfamiliar links or attachments
- Don’t answer or reply to emails or messages from unknown senders or sources
- Always log into your everyday accounts through a new browser tab or the official app − never from a link sent in an email or text
- Never share any personally identifiable information (PII) with anyone other than your authorised institutions (banks, online social services, telco providers, etc.)
- Use a combination of anti-virus software, spoofing detection software, and email spam filters to detect and block infected emails
- Check every URL carefully before clicking on a website (there are free online tools available for URL scanning), and only access URLs that begin with HTTPS
- Carefully read every communication you receive (spoof attacks usually contain poor grammar or unnatural sentence structures)
- Enable multi-factor authentication (MFA) and password protection whenever possible.
The best way to avoid spoofing attacks is to keep your wits about you, stick to company policies if you work for a business, and flag any suspicious activity.
Spoofing vs phishing: What’s the difference?
Phishing and spoofing are similar on the surface, but there’s a slight difference worth noting. Spoofing is a hybrid between a phishing attack and an impersonation scam. Spoofers try to trick victims into handing over confidential information by masquerading as a legitimate person, business, or organisation.
On the other hand, phishing relies mainly on social engineering techniques to trick users into giving away their personal information. Phishing also rarely involves the use of malicious software and relies mostly on ‘human hacking’. In spoofing, malicious software is installed on the target computer or network.
A final word
Spoofing attacks can happen to anyone which is why it’s important to have airtight cyber security defences to keep malware at bay, protect your network and traffic, and to remain extra vigilant to phishing and other social engineering attacks. For more tips on how to stay safe online, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


